Does the Cisco 300-206 dumps seem like a waste of money to other folks? The Implementing Cisco Edge Network Security Solutions (300-206 SENSS) exam is a 90 minutes (65 – 75 questions) assessment in pass4itsure that is associated with the CCNP Security certification. 100% free Cisco 300-206 dumps SENSS exam questions Implementing Cisco Edge Network Security Solutions video study. “Implementing Cisco Edge Network Security Solutions” is the exam name of Pass4itsure Cisco 300-206 dumps test which designed to help candidates prepare for and pass the Cisco 300-206 exam. SENSS 300-206 discount coupons and upcoming offerings are also there for latest techniques and learning modes. There are promotional coupons too to facilitate the https://www.pass4itsure.com/300-206.html Implementing Cisco Edge Network Security Solutions (SENSS) test student with our upcoming technologies and methods.
[New Pass4itsure 300-206 Dumps Questions From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWam9uZE5CQl9jczA
[New Pass4itsure 642-732 Dumps Questions From Google Drive]: https://drive.google.com/open?id=1qyX5atfYORjOT6lNPg41yUJwrSgZpDR-

Kill your exam with Cisco 300-206 dumps real questions(1-34)
QUESTION 1
What is the primary purpose of stateful pattern recognition in Cisco IPS networks?
A. mitigating man-in-the-middle attacks
B. using multipacket inspection across all protocols to identify vulnerability-based attacks and to thwart attacksthat hide within a data stream
C. detecting and preventing MAC address spoofing in switched environments
D. identifying Layer 2 ARP attacks
300-206 exam Correct Answer: B
QUESTION 2
In which two modes is zone-based firewall high availability available? (Choose two.)
A. IPv4 only
B. IPv6 only
C. IPv4 and IPv6
D. routed mode only
E. transparent mode only
F. both transparent and routed modes
Correct Answer: CD
QUESTION 3
Enabling what security mechanism can prevent an attacker from gaining network topology information from CDP via a man-in-the-middle attack?
A. MACsec
B. Flex VPN
C. Control Plane Protection
D. Dynamic Arp Inspection
300-206 dumps Correct Answer: A
QUESTION 4
When configured in accordance to Cisco best practices, the ip verify source command can mitigate which two types of Layer 2 attacks? (Choose two.)
A. rogue DHCP servers
B. ARP attacks
C. DHCP starvation
D. MAC spoofing
E. CAM attacks
F. IP spoofing
Correct Answer: DF
QUESTION 5
Which three configurations are needed to enable SNMPv3 support on the Cisco ASA? (Choose three.)
A. SNMPv3 Local EngineID
B. SNMPv3 Remote EngineID
C. SNMP Users
D. SNMP Groups
E. SNMP Community Strings
F. SNMP Hosts
300-206 pdf Correct Answer: CDF
QUESTION 6
A network printer has a DHCP server service that cannot be disabled. How can a layer 2 switch be configured to prevent the printer from causing network issues?
A. Remove the ip helper-address
B. Configure a Port-ACL to block outbound TCP port 68
C. Configure DHCP snooping
D. Configure port-security
Correct Answer: C
QUESTION 7
Which command sets the source IP address of the NetFlow exports of a device?
A. ip source flow-export
B. ip source netflow-export
C. ip flow-export source
D. ip netflow-export source
300-206 vce Correct Answer: C
QUESTION 8
At which layer does MACsecprovide encryption?
A. Layer 1
B. Layer 2
C. Layer 3
D. Layer 4
Correct Answer: B
QUESTION 9
Where on a firewall does an administrator assign interfaces to contexts?
A. in the system execution space
B. in the admin context
C. in a user-defined context
D. in the console
300-206 exam Correct Answer: A
QUESTION 10
Which two TCP ports must be open on the Cisco Security Manager server to allow the server to communicate with the Cisco Security Manager client? (Choose two.)
A. 1741
B. 443
C. 80
D. 1740
E. 8080
Correct Answer: AB
QUESTION 11
Which Layer 2 security feature prevents traffic on a LAN from being disrupted by a broadcast,multicat, or unicast storm on one physical interface?
A. Bridge protocol Data Unit Guard
B. Storm Control
C. Embedded event monitoring
D. Access control lists
300-206 dumps Correct Answer: B
QUESTION 12
Which function does DNSSEC provide in a DNS infrastructure?
A. It authenticates stored information.
B. It authorizes stored information.
C. It encrypts stored information.
D. It logs stored security information.
Correct Answer: A
QUESTION 13
By default, not all services in the default inspection class are inspected. Which Cisco ASA CLI command do you use to determine which inspect actions are applied to the default inspection class?
A. show policy-map global_policy
B. show policy-map inspection_default
C. show class-map inspection_default
D. show class-map default-inspection-traffic
E. show service-policy global
300-206 pdf Correct Answer: E
QUESTION 14
Which statement describes the correct steps to enable Botnet Traffic Filtering on a Cisco ASA version 9.0 transparent mode firewall with an active Botnet Traffic Filtering license?
A. Enable DNS snooping, traffic classification, and actions.
B. Botnet Traffic Filtering is not supported in transparent mode.
C. Enable the use of the dynamic database, enable DNS snooping, traffic classification, and actions.
D. Enable the use of dynamic database, enable traffic classification and actions.
Correct Answer: C
QUESTION 15
Refer to the exhibit.

Which two statements about this firewall output are true? (Choose two.)
A. The output is from a packet tracer debug.
B. All packets are allowed to 192.168.1.0 255.255.0.0.
C. All packets are allowed to 192.168.1.0 255.255.255.0.
D. All packets are denied.
E. The output is from a debug all command.
300-206 vce Correct Answer: AC
QUESTION 16
In which way are management packets classified on a firewall that operates in multiple context mode?
A. by their interface IP address
B. by the routing table
C. by NAT
D. by their MAC addresses
Correct Answer: A
QUESTION 17
Which option is the default logging buffer size In memory of the Cisco ASA adaptive security appliance?
A. 8KB
B. 32KB
C. 2KB
D. 16KB
E. 4KB
300-206 exam Correct Answer: E
QUESTION 18
A network administrator is creating an ASA-CX administrative user account with the following parameters: -The user will be responsible for configuring security policies on networkdevices.
-The user needs read-write access to policies.
-The account has no more rights than necessary for the job.
What role will be assigned to the user?
A. Administrator
B. Security administrator
C. System administrator
D. Root Administrator
E. Exec administrator
Correct Answer: B
QUESTION 19
What are three attributes that can be applied to a user account with RBAC? (Choose three.)
A. domain
B. password
C. ACE tag
D. user roles
E. VDC group tag
F. expiry date
300-206 dumps Correct Answer: BDF
QUESTION 20
Which two router commands enable NetFlow on an interface? (Choose two.)
A. ip flow ingress
B. ip flow egress
C. ip route-cache flow infer-fields
D. ip flow ingress infer-fields
E. ip flow-export version 9
Correct Answer: AB
QUESTION 21
At which firewall severity level will debugs appear on a Cisco ASA?
A. 7
B. 6
C. 5
D. 4
300-206 pdf Correct Answer: A
QUESTION 22
What are two high-level task areas in a Cisco Prime Infrastructure life-cycle workflow? (Choose two.)
A. Design
B. Operate
C. Maintain
D. Log
E. Evaluate
Correct Answer: AB
QUESTION 23
Refer to the exhibit.

Which option describes the expected result of the capture ACL?
A. The capture is applied, but we cannot see any packets in the capture
B. The capture does not get applied and we get an error about mixed policy.
C. The capture is applied and we can see the packets in the capture
D. The capture is not applied because we must have a host IP as the source
300-206 vce Correct Answer: B
QUESTION 24
A network engineer is troubleshooting and configures the ASA logging level to debugging. The logging-buffer is dominated by %ASA-6-305009 log messages. Which command suppresses those syslog messages while maintaining ability to troubleshoot?
A. no logging buffered 305009
B. message 305009 disable
C. no message 305009 logging
D. no logging message 305009
Correct Answer: D
QUESTION 25
For which purpose is the Cisco ASA CLI command aaa authentication match used?
A. Enable authentication for SSH and Telnet connections to the Cisco ASA appliance.
B. Enable authentication for console connections to the Cisco ASA appliance.
C. Enable authentication for connections through the Cisco ASA appliance.
D. Enable authentication for IPsec VPN connections to the Cisco ASA appliance.
E. Enable authentication for SSL VPN connections to the Cisco ASA appliance.
F. Enable authentication for Cisco ASDM connections to the Cisco ASA appliance.
300-206 exam Correct Answer: C
QUESTION 26
When it is configured in accordance to Cisco best practices, the switchport port-security maximum command can mitigate which two types of Layer 2 attacks? (Choose two.)
A. rogue DHCP servers
B. ARP attacks
C. DHCP starvation
D. MAC spoofing
E. CAM attacks
F. IP spoofing
Correct Answer: CE
QUESTION 27
When a traffic storm threshold occurs on a port, into which state can traffic storm control put the port?
A. Disabled
B. Err-disabled
C. Disconnected
D. Blocked
E. Connected
300-206 dumps Correct Answer: B
QUESTION 28
How many interfaces can a Cisco ASA bridge group support and how many bridge groups can a Cisco ASA appliance support?
A. up to 2 interfaces per bridge group and up to 4 bridge groups per Cisco ASA appliance
B. up to 2 interfaces per bridge group and up to 8 bridge groups per Cisco ASA appliance
C. up to 4 interfaces per bridge group and up to 4 bridge groups per Cisco ASA appliance
D. up to 4 interfaces per bridge group and up to 8 bridge groups per Cisco ASA appliance
E. up to 8 interfaces per bridge group and up to 4 bridge groups per Cisco ASA appliance
F. up to 8 interfaces per bridge group and up to 8 bridge groups per Cisco ASA appliance
Correct Answer: D
QUESTION 29
Refer to the exhibit.
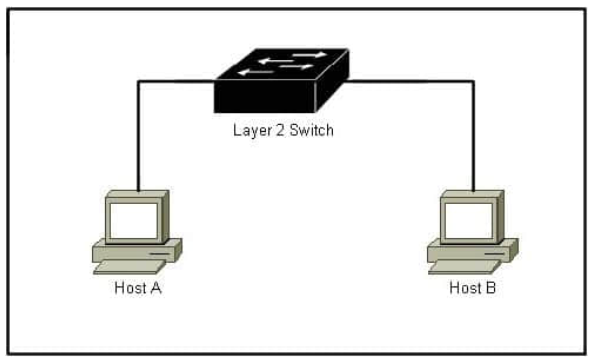
To protect Host A and Host B from communicating with each other, which type of PVLAN port should be used for each host?
A. Host A on a promiscuous port and Host B on a community port
B. Host A on a community port and Host B on a promiscuous port
C. Host A on an isolated port and Host B on a promiscuous port
D. Host A on a promiscuous port and Host B on a promiscuous port
E. Host A on an isolated port and host B on an isolated port
F. Host A on a community port and Host B on a community port
300-206 pdf Correct Answer: E
QUESTION 30
Which two option are protocol and tools are used by management plane when using cisco ASA general management plane hardening ?
A. Unicast Reverse Path Forwarding
B. NetFlow
C. Routing Protocol Authentication
D. Threat detection
E. Syslog
F. ICMP unreachables
G. Cisco URL Filtering
Correct Answer: BE
QUESTION 31
Which option is a different type of secondary VLAN?
A. Transparent
B. Promiscuous
C. Virtual
D. Community
300-206 vce Correct Answer: D
QUESTION 32
Which five options are valid logging destinations for the Cisco ASA? (Choose five.)
A. AAA server
B. Cisco ASDM
C. buffer
D. SNMP traps
E. LDAP server
F. email
G. TCP-based secure syslog server
Correct Answer: BCDFG
QUESTION 33
Which statement about the Cisco ASA configuration is true?
A. All input traffic on the inside interface is denied by the global ACL.
B. All input and output traffic on the outside interface is denied by the global ACL.
C. ICMP echo-request traffic is permitted from the inside to the outside, and ICMP echo- reply will be permittedfrom the outside back to inside.
D. HTTP inspection is enabled in the global policy.
E. Traffic between two hosts connected to the same interface is permitted.
300-206 exam Correct Answer: B
QUESTION 34
Cisco Security Manager can manage which three products? (Choose three.)
A. Cisco IOS
B. Cisco ASA
C. Cisco IPS
D. Cisco WLC
E. Cisco Web Security Appliance
F. Cisco Email Security Appliance
G. Cisco ASA CX
H. Cisco CRS
Correct Answer: ABC

See What Our Customers Are Saying:
We at Pass4itsure are committed to our customer’s success. There are 50,000+ customers who used this preparation material for the preparation of various certification exams and this number of customers is enough for new candidates to trust in these products.Our Cisco 300-206 dumps are created with utmost care and professionalism. We utilize the experience and knowledge of a team of industry professionals from leading organizations all over the world.
Pass4itsure Cisco 300-206 dumps reasonable price offerings are not only for existing Implementing Cisco Edge Network Security Solutions (SENSS) exam students but also for the new IT students. “Implementing Cisco Edge Network Security Solutions”, also known as 300-206 exam, is a Cisco certification which covers all the knowledge points of the real Cisco exam. Pass4itsure Cisco 300-206 dumps exam questions answers are updated (254 Q&As) are verified by experts. The associated certifications of 300-206 dumps is CCNP Security. Get our Cisco https://www.pass4itsure.com/300-206.html dumps pdf and ensure your development and growth in IT field. You can purchase it from easy online money payment methods.
Read More Youtube: https://youtu.be/Dt7R-PmVdMw
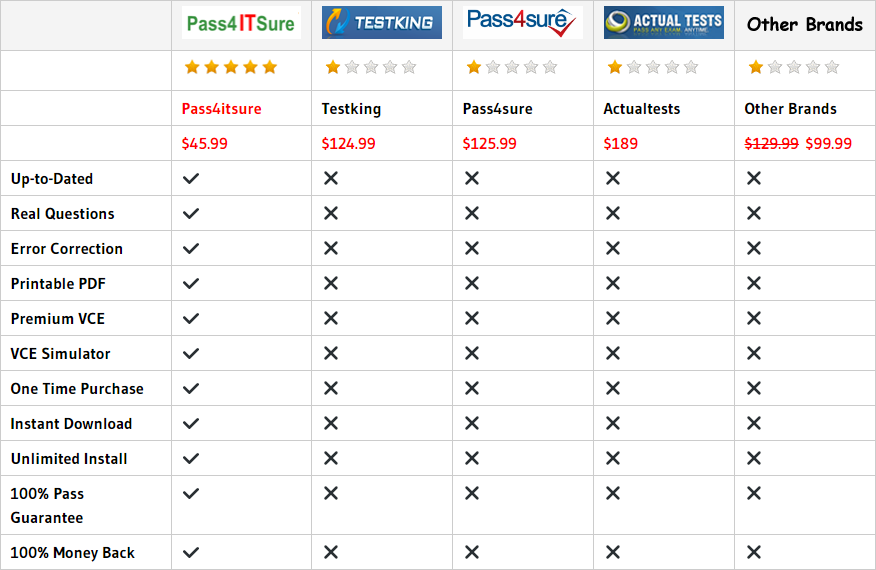
Compared with other brands, Pass4itsure has up to dated exam information, affordable price, instant exam PDF files downloaded, error correction, unlimited install,etc. Such as Pass4itsure Cisco 300-206 Dumps Q&A, Best Quality Cisco 300-206 Dumps Exam Materials Are Based On The Real Exam, We Help You Pass Implementing Cisco Edge Network Security Solutions. Simple and Easy! To take advantage of the guarantee, simply contact Customer Support, requesting the exam you would like to claim. Pass4itsure guarantee insures your success otherwise get your MONEYBACK!
The post [New Questions] 100% Free Cisco 300-206 Dumps SENSS Exam Questions Implementing Cisco Edge Network Security Solutions Video Study (Question 1 – Question 34) appeared first on Real IT Certification Training: Pass Exam & Get Certified.